
African banks heavily targeted in RemcosRAT malware campaigns


African banks are increasingly targeted by malware distribution campaigns that employ HTML smuggling tricks and typo-squatted domains to drop remote access trojans (RATs).
Cybercriminals interested in quick financial gains are a constant source of trouble for banks in Africa, which have resorted to deploying strict gateway security controls.
This has forced the threat actors to craft more clever attacks that could bypass the protection measures, and in 2022, bank-targeting campaigns are seen using a combination of tricks.
One of those 2022 campaigns was discovered by HP Wolf Security, whose analysts looked into the adversary’s tactics and the infection steps they follow.
The lure
The attack begins with a phishing email sent to a bank employee from a typo-squatted domain that resembles the URL of a legitimate company, typically a competitor bank.
The email presents the recipient with a lucrative job offer and links to the details on the said site. Following that link takes the victim to a webpage containing application instructions.
.png)
The content of this page is copied from an actual listing by the mimicked bank, so the details there appear convincingly realistic.
These sites don’t perform phishing or host malware, so their sole purpose is to lead the victim down the infection path.
The payload
The payload arrives in the form of an HTML attachment on the said email message, which is a base64-encoded ISO archive file decoded on the fly and offered for download via a JavaScript blob on the browser.
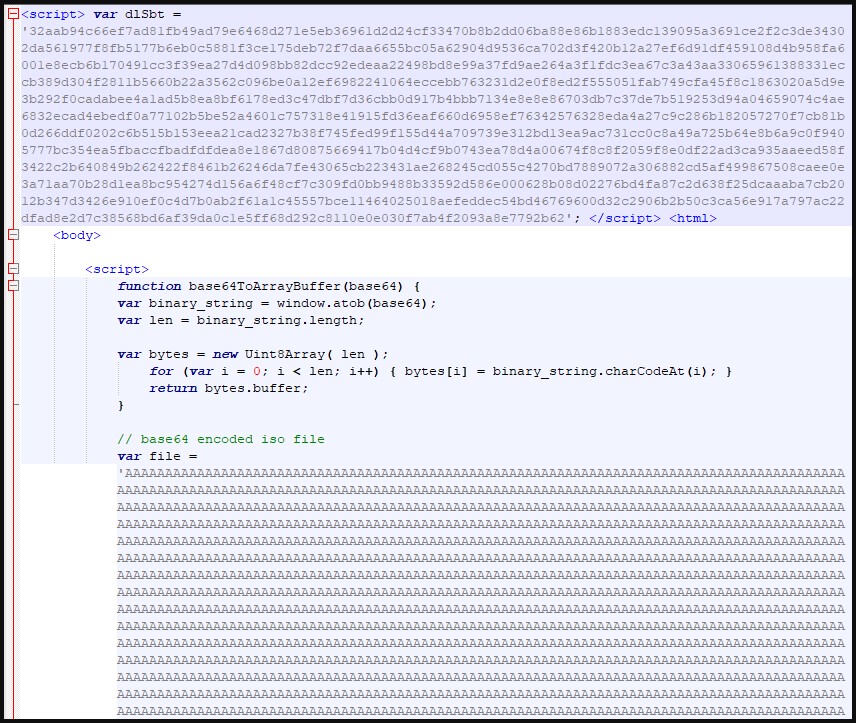
This technique of sneaking risky file formats without raising alarms from email security products is called HTML smuggling, and it’s a well-established and trending payload distribution method.
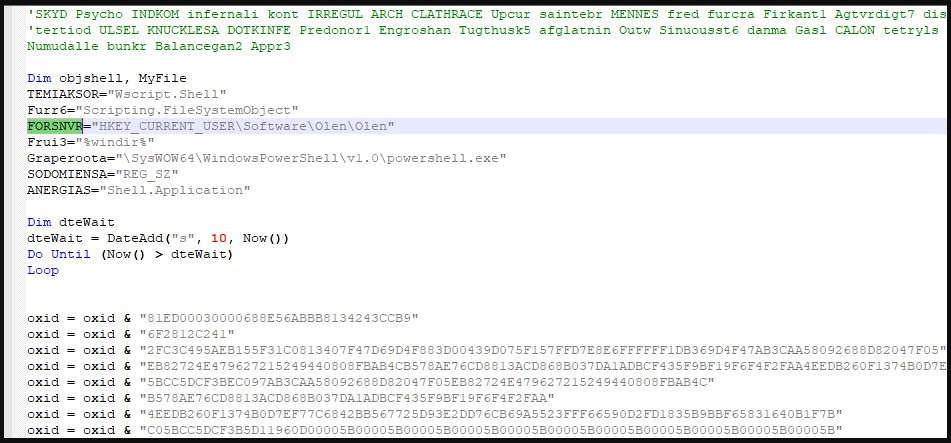
The ISO file contains a Visual Basic Script (VBS) file, which executes upon double click to create a new Registry key and run PowerShell commands that call various Windows API functions.
After a series of malicious code executions and Windows API abuse, GuLoader is assembled on the system and executed to download and runs the RemcosRAT malware.
According to HP’s threat analysts, GuLoader has two download URLs in its configuration, one pointing to Dropbox and one to OneDrive, so there’s some redundancy implemented at this stage.
It is also important to note that GuLoader is executed via PowerShell stored in the registry, and runs on the system memory, so most anti-virus tools won’t detect it.
As HP points out, the only way to break the infection chain would be to set the default application for script files from Windows Script Host to Notepad, which would reveal the real nature of the VBS file.
The goal
Remcos is an otherwise legitimate commercial remote access tool (RAT) that has been used by cybercriminals for malicious purposes for several years now.
It’s a powerful tool supporting remote command execution, screenshot capturing, keystroke logging, webcam and microphone recording, and more.
Potentially, the threat actors use Remcos to sniff on transaction details, steal valuable credentials, move laterally in the bank’s network, or steal information needed for BEC attacks.
Financial extortion via data exfiltration or ransomware deployment is also likely, while the threat actors can always opt to sell their network access to other hackers and make a quick buck without risking law enforcement trouble.
Source: https://www.bleepingcomputer.com/news/security/african-banks-heavily-targeted-in-remcosrat-malware-campaigns/


















