
Bearded Barbie hackers catfish high ranking Israeli officials


The Hamas-backed hacking group tracked as ‘APT-C-23’ was found catfishing Israeli officials working in defense, law, enforcement, and government agencies, ultimately leading to the deployment of new malware.
The campaign involves high-level social engineering tricks such as creating fake social media profiles and a long-term engagement with the targets before delivering spyware.
According to analysts at Cybereason, who named this new campaign ‘Operation Bearded Barbie,’ APT-C-23 is also deploying new custom backdoors for Windows and Android devices geared towards espionage.
Fake Facebook profiles
The threat actors have created several fake Facebook profiles using fabricated identities and stolen or AI-generated images of attractive women and approach the targets through these profiles.
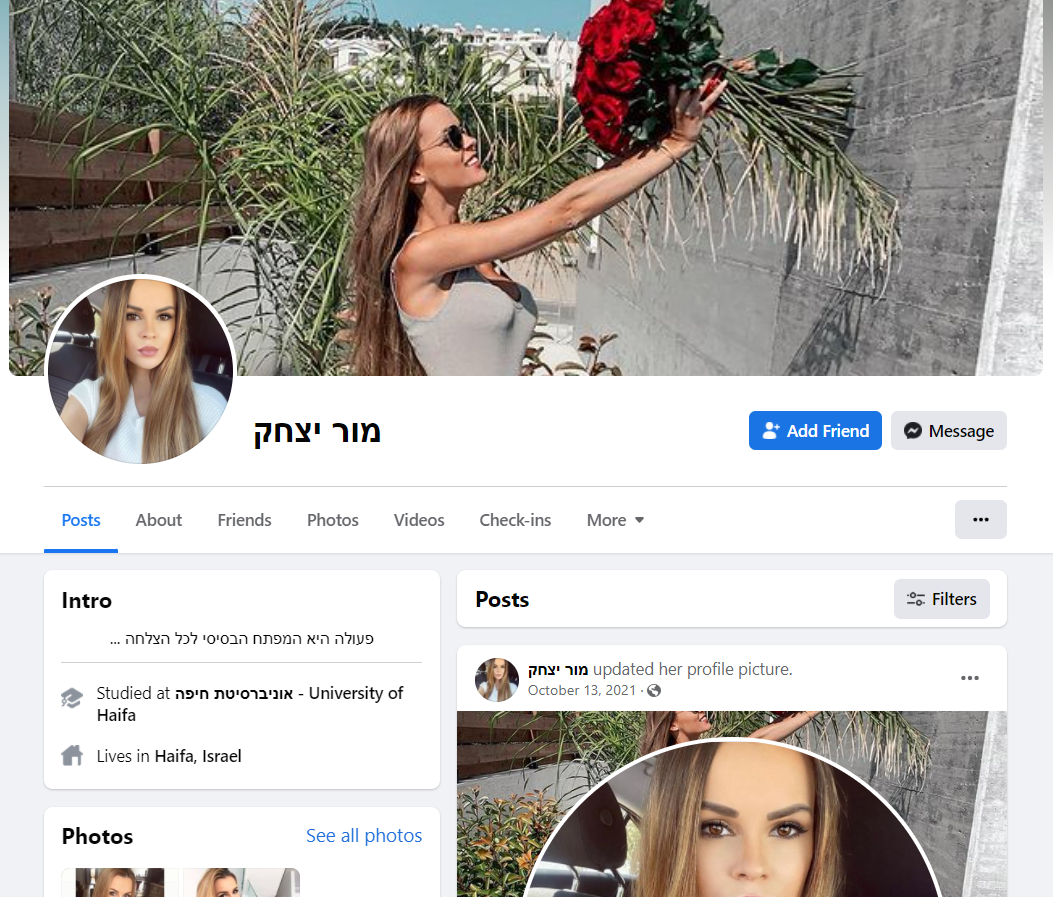
To make them appear authentic, the operators have curated these profiles for months, posting in Hebrew and liking groups and popular pages in Israel.
The operators of these profiles build an entire network of friends who are, in reality, targeted people working in Israel’s police, defense forces, emergency services, or the government.
After gaining the trust of the target by interacting with them for a while, the adversaries suggest migrating the conversation to WhatsApp, supposedly for better privacy.
This is when the conversation takes an erotic turn, with the threat actors suggesting another pivot to a supposedly more discreet Android IM app, which is actually the VolatileVenom malware.
Simultaneously, the operative sends a link to a RAR file that purportedly contains a sexual video, but which in reality is a downloader for the BarbWire backdoor.
.jpg)
Refreshed Android spyware
Starting with VolatileVenom, this Android malware disguises itself as a messaging app, most frequently Wink Chat.
.jpg)
(Cybereason)
Cybereason clarifies that this backdoor has been used by APT-C-23 since at least April 2020, but it has been enriched with additional features since then.
During the first launch and sign-up process, the app displays a bogus error and declares it will automatically remove itself from the device.
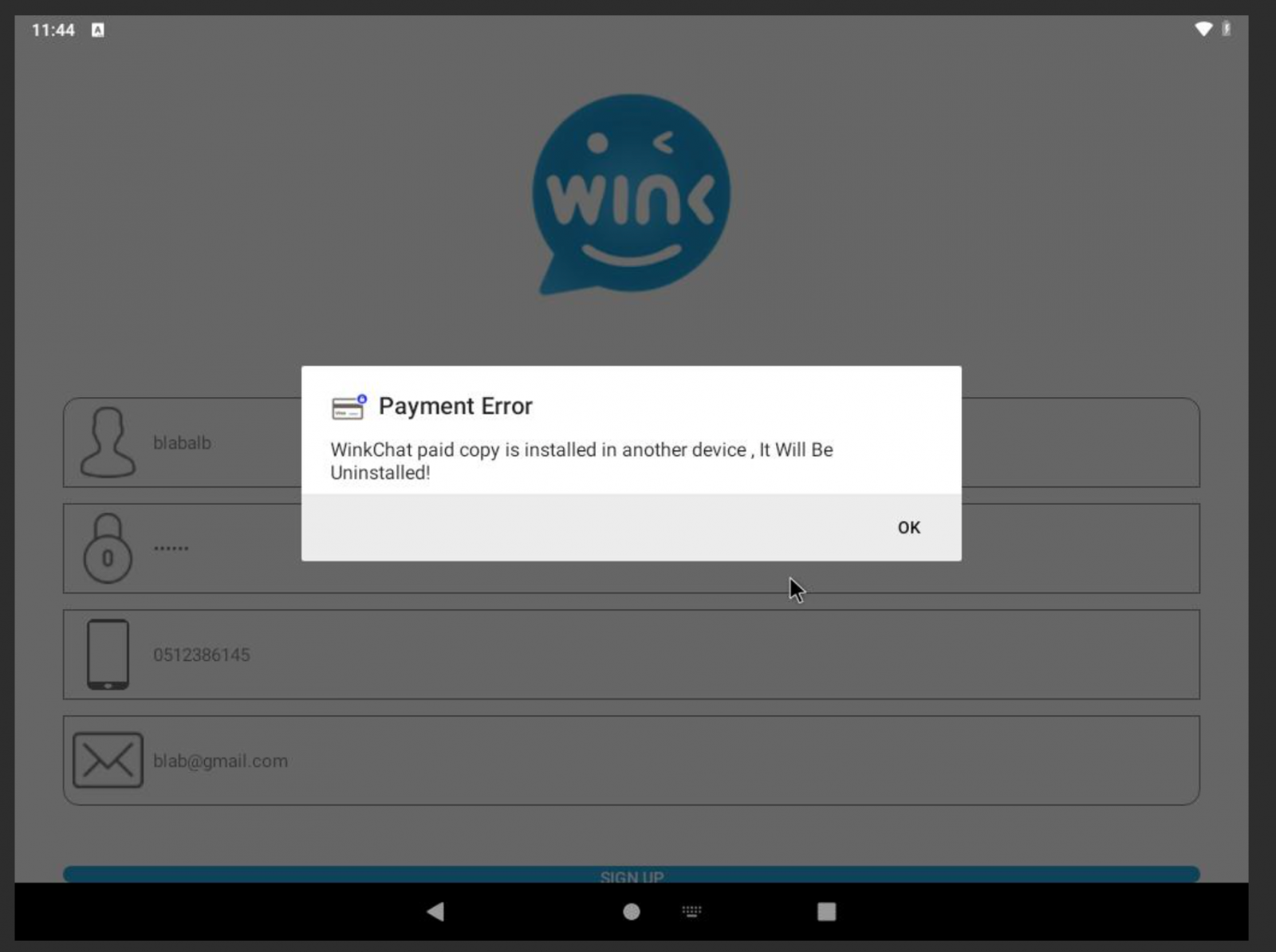
In reality, though, it continues to run in the background, performing the following functions:
- Steal SMS messages
- Read contact list information
- Use the device camera to take photos
- Steal files with the following extensions: pdf, doc, docs, ppt, pptx, xls, xlsx, txt, text
- Steal images with the following extensions: jpg, jpeg, png
- Record audio
- Use Phishing to steal credentials to popular apps such as Facebook and Twitter
- Discard system notifications
- Get installed applications
- Restart Wi-Fi
- Record calls / WhatsApp calls
- Extract call logs
- Download files to the infected device
- Take screenshots
- Read notifications of the following apps: WhatsApp, Facebook, Telegram, Instagram, Skype, IMO, Viber
- Discards any notifications raised by the system
If the victim’s device runs Android 10 or later, the app will use a Google Play, Chrome, or Google Maps icon. On earlier Android versions, it hides its app icon completely.
Barb(ie) and BarbWire malware
As part of the catfish attempts, the threat actors will eventually send the target a RAR file that is allegedly nude photos or videos.
However, this RAR file contains the Barb(ie) downloader malware, which leads to the installation of the BarbWire backdoor.
A sample of Barb(ie) seen by Cybereason has the file name “Windows Notifications,” and when launched, will perform some anti-analysis checks.
Next, Barb(ie) connects to the command and control servers (C2) and sends a system ID profile, while it also establishes persistence by creating two scheduled tasks. Finally, it downloads and installs the BarbWire backdoor on the device.
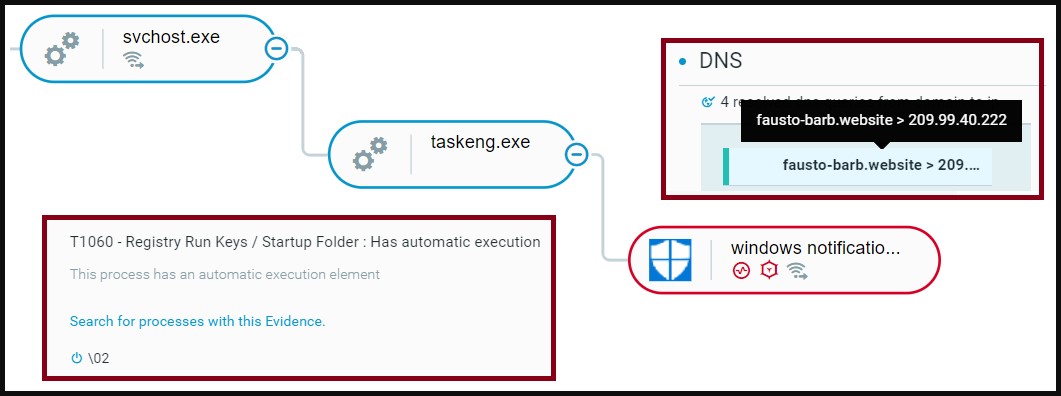
BarbWire is a fully-fledged backdoor with extensive capabilities such as:
- Persistence
- OS Reconnaissance (username, architecture, Windows version, installed AV products)
- Data encryption
- Keylogging
- Screen capturing
- Audio recording
- Download additional malware
- Local/external drives and directory enumeration
- Steal specific file types and exfiltrate data in RAR form
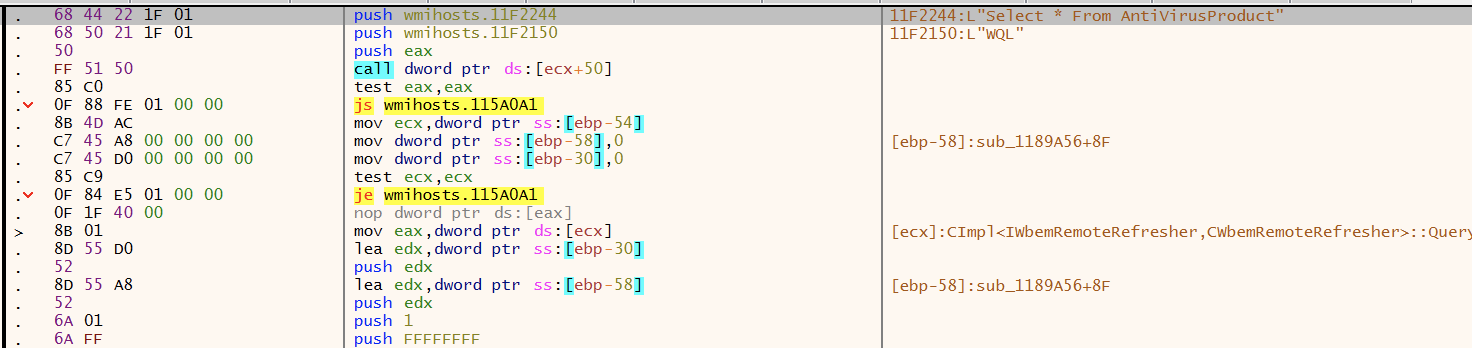
Cybereason was able to sample at least three different variants of BarbWire, which indicates its active development by the APT-C-23 group.
Evolving campaigns
APT-C-23 uses many techniques that we have seen employed in many past campaigns against Israeli targets but continues to evolve with new tools and more complex social engineering efforts.
One point of differentiation between Operation Bearded Barbie and previous campaigns is that there is no overlapping infrastructure, showing the group’s interest in avoiding detection.
The use of two backdoors, one for Windows and one for Android, is another escalation for the threat actor, resulting in very aggressive espionage for the compromised targets.
Source: https://www.bleepingcomputer.com/news/security/bearded-barbie-hackers-catfish-high-ranking-israeli-officials/


















