
DarkHotel hacking campaign targets luxury Macao resorts


The South Korean DarkHotel hacking group has been spotted in a new campaign spanning December 2021 through January 2022, targeting luxury hotels in Macao, China.
DarkHotel is a sophisticated hacking group targeting the hospitality industry to conduct high-level espionage or data monetization via dark web sales.
Macao is an autonomous region in South China, near Hong Kong, enjoying a steady influx of leisure and business tourists. Its giant casinos and malls have earned Macao the nickname “Las Vegas of Asia.”
The region is of particular interest to DarkHotel, which targets hotel systems to intercept guest browsing data via the WiFi network.
The latest observation of DarkHotel activity comes from threat analysts at Trellix, who has tracked the C2 IP address exposed in a December 2021 report by Zscaler to trace the actor’s activity.
Strangely, DarkHotel didn’t bother to move its operation to different infrastructure after the exposure of their attack identifiers; hence Trellix’s subsequent tracking was made possible.
The Macao campaign
Two of the hotel chains confirmed as targeted in this campaign are the Grand Coloane Resort and the Wynn Palace, both 5-star hotels.
These hotels were planning to host international conferences on trade, investment, and the environment, so DarkHotel’s campaign was likely aiming to lay the foundation for future espionage.
.jpg)
Trellix logged the first phishing emails of the threat group on December 7, 2021, sent to seventeen hotels from an address impersonating the Macao Government Tourism Office.
The attached Excel file that supposedly contained important information to hotel operators had malicious macro code in obfuscated form.
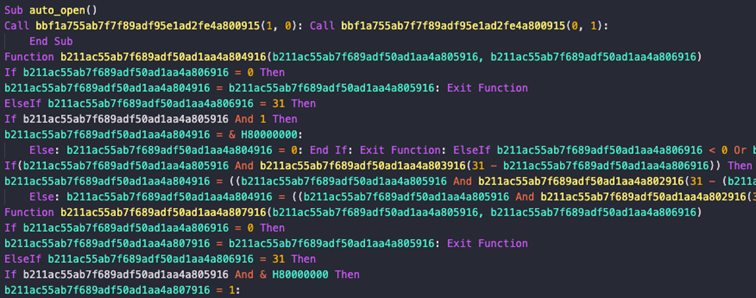
Upon opening the file and enabling content on the Microsoft Office Suite, the document loads the Task Scheduler Service and drops a VBS script in a system folder.
From there, the malware can launch PowerShell and wscript.exe to obtain host system details and send them to the C2 server, in this case, “https://fsm-gov[.]com”.
.png)
This is a spoofed domain impersonating the actual website of the Government of the Federated States of Micronesia, which is on “.fsmgov.org.”
By investigating further, Trellix found out that the C2’s backend is similar to those previously reported and associated with DarkHotel, and also discovered the abuse of Mailman for the distribution of the phishing emails.
On January 18, 2022, and soon after the mentioned hotels announced the postponement of the conferences due to COVID-19, the threat actor stopped the email distribution.
Attribution
Trellix isn’t entirely confident regarding the attribution of this campaign, but they have key evidence that points to the South Korean threat actors.
- The first is using the same C2 IP address as that reported by Zscaler.
- Secondly, the targeted entities and the apparent campaign goals match DarkHotel’s operational approach.
- Thirdly, the C2 panel closely resembles those previously used by the group.
The only issue that brings doubt is the persistence in using the particular IP address after its public exposure, which doesn’t match the OPSEC level of a sophisticated actor.
Moreover, Trellix has seen other malicious activities stemming from the same IP address that doesn’t appear to be related to DarkHotel.
One potential explanation for this is that DarkHotel purposefully used this common IP address with other threat actors to obscure its trace by hiding behind other activities.
Trellix has informed the Macao Security Forces Affairs Bureau of this campaign, so the concerned parties are monitoring the situation.
Hotel guests using hotel WiFi to connect are advised to use a VPN tool to keep their network traffic encrypted in the case it gets intercepted.
Source: https://www.bleepingcomputer.com/news/security/darkhotel-hacking-campaign-targets-luxury-macao-resorts/


















