UPS flaws allow for remote code execution and remote fire-based interruptions
Security researchers at Armis have detailed a trio of vulnerabilities in so-called Smart-UPS devices sold by Schneider Electric subsidiary APC that allow for unnoticeable remote code execution, replacing of firmware, and potentially burning out the entire unit.
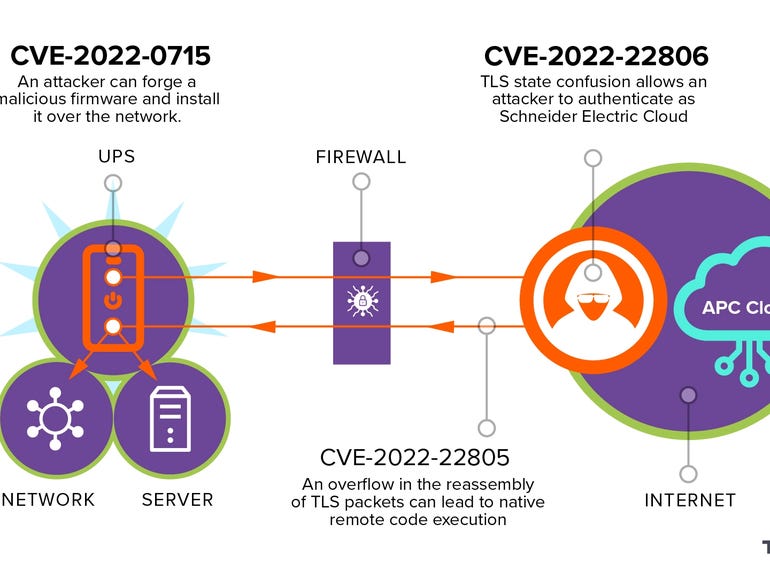
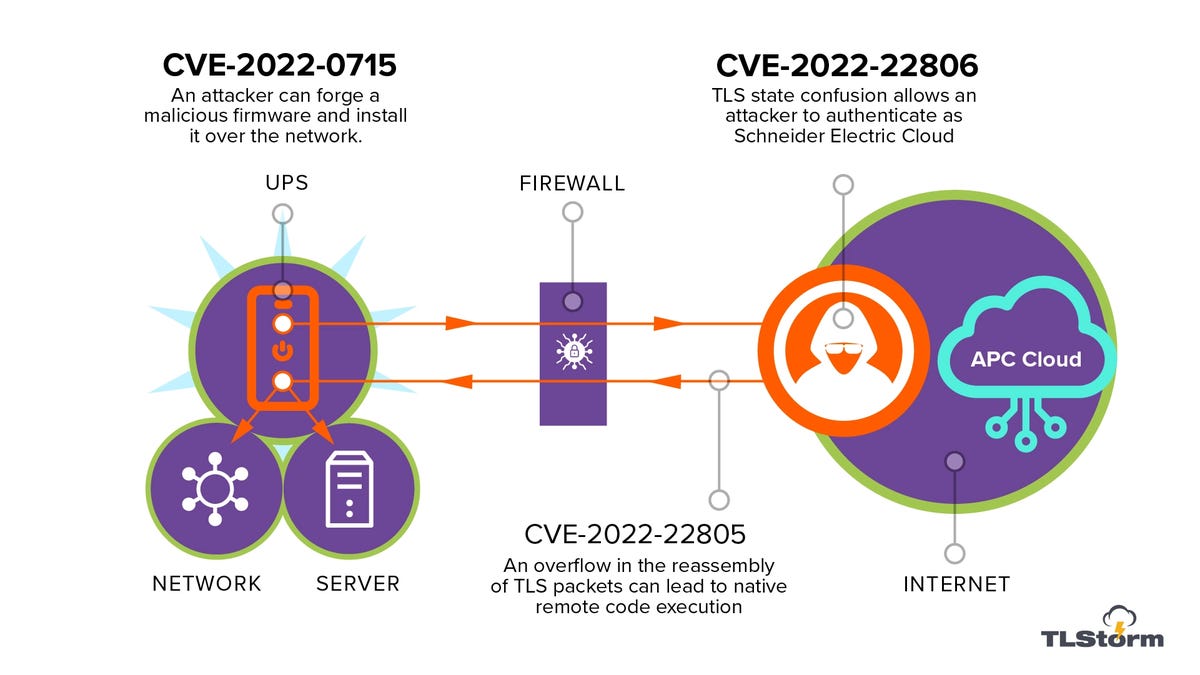
Naturally in 2022, the flaws in the system stem from a combination of bad TLS implementation and being able to be controlled through a cloud-based system in newer devices.
“Since the TLS attack vector can originate from the internet, these vulnerabilities can act as a gateway to the internal corporate network. Bad actors can use the TLS state confusion to identify themselves as the Schneider Electric cloud and collect information about the UPS behind the corporate firewall,” Armis said.
“They can then remotely update the UPS firmware and use the UPS as the entry point for a ransomware attack or any other type of malicious operation.”
If a TLS connection has an error, rather than closing the connection as recommended by Mocana nanoSSL library writers, APC ignores some of the errors, which leaves the connection open and the library in a state it is not built to handle.
“Ignoring the nanoSSL library errors causes the UPS to cache the TLS key in its uninitialized state,” Arris said.
“When an attacker uses the TLS resumption functionality, the uninitialized key (all zero) is fetched from the cache and the attacker can communicate with the device as if it was a genuine Schneider Electric server. As a seemingly verified server, the attacker can issue a firmware upgrade command and remotely execute code over the UPS device.”
Additionally, all Smart-UPS devices use the same symmetric key for encryption and decryption, and it can be extracted from the devices. As a bonus, the devices do not check if any firmware is signed, allowing attackers to remain persistently on the device.

In the words of the Bloodhound Gang: We don’t need no water.
Image: ArmisOn the extreme physical end of the equation, replacing the firmware allows an attacker bypass software-based physical protections, such as a short circuit alert turning off the UPS.
“By using our RCE vulnerability we were able to bypass the software protection and let the current spike periods run over and over until the DC link capacitor heated up to ~150 degrees celsius (~300F), which caused the capacitor to burst and brick the UPS in a cloud of electrolyte gas, causing collateral damage to the device,” the researchers state in a white paper [PDF].
“The exploitation risk is no longer limited to the IT world — an attacker can turn the UPS to a physical weapon. From a cyber security point of view, these kinds of systems must be handled as a flammable substance that sits in the heart of an organization.”
Armis recommends users install the patches from Schneider Electric, and use access control lists to restrict and encrypt communications with the UPS to management devices and Schneider Electric Cloud. If the device has a network management card, Armis recommends changing the default password from “apc” to something else, and installing a publicly-signed certificate to prevent password sniffing.
The security company said it believes 80% of organisations are vulnerable, with healthcare organisations hitting over 92% with a vulnerable device and retail just behind on 89%.
Updated at 3:52pm AEST, 9 March 2022: Clarified technical information.
Related Coverage
- Tampering with ACT overseas e-voting system did not need key, researcher finds
- SSL certificate research highlights pitfalls for company data, competition
- HTTPS threats grow more than 314% through 2021: Report
- Manual certificate management falling way behind PKI growth
- In-the-wild DDoS attack can be launched from a single packet to create terabytes of traffic
- Cloudflare and Akamai refuse to pull services out of Russia
Source: https://www.zdnet.com/article/ups-flaws-allow-for-remote-code-execution-and-remote-fire-based-interruptions/#ftag=RSSbaffb68