
Roaming Mantis Android malware campaign sets sights on Europe


The Roaming Mantis SMS phishing campaign has finally reached Europe, as researchers detect campaigns targeting Android and iPhone users in Germany and France with malicious apps and phishing pages.
Roaming Mantis is a credential theft and malware distribution campaign that uses SMS phishing (smishing) to distribute malicious Android apps as standalone APK files outside the Google Play Store.
Over the past four years, the campaign has been under constant evolution and was first spotted in 2018, targeting Android smartphone users in Japan via DNS hacking.
It later evolved to target iOS users with phishing pages for credential theft and expand the targeted countries to include Taiwan and Korea.
Fake shipping texts
In its most recent form, Roaming Mantis uses a trojan named ‘Wroba,’ and is targeting users in France and Germany with smishing messages and landing pages injected on compromised legitimate websites.
The goal of Wroba is to steal e-banking details, and like other similar trojans, it spreads automatically using SMS phishing texts to people in the infected device’s contacts.
The infection chain starts with the arrival of an SMS text on the target device, which contains a short warning message about a shipped package with an included URL.
.
If the URL is clicked from an Apple device, it redirects the victim to a phishing page, where it attempts to steal the user’s Apple login credentials.
However, if the victim uses an Android device, they are taken to a landing page that prompts them to install malware disguised as an Android app.
The impersonated apps that contain the Wroba are predominantly for Google Chrome but also imitate the Yamato transport and ePOST apps.
Below are the download stats from a single day in September 2021, counting tens of thousands of malicious APK downloads in Europe.

Source: Kaspersky
Now stealing your images and videos
Compared to past variants, the Wrogba loader and payload have evolved and are now written in Kotlin, a language with excellent interoperability with Java.
The backdoor includes 21 malicious commands that can be executed by the attacks, with two new ones added in recent campaigns. These new commands are “get_gallery” and “get_photo,” which are meant to steal the victim’s photos and videos and upload them to the attacker’s servers.
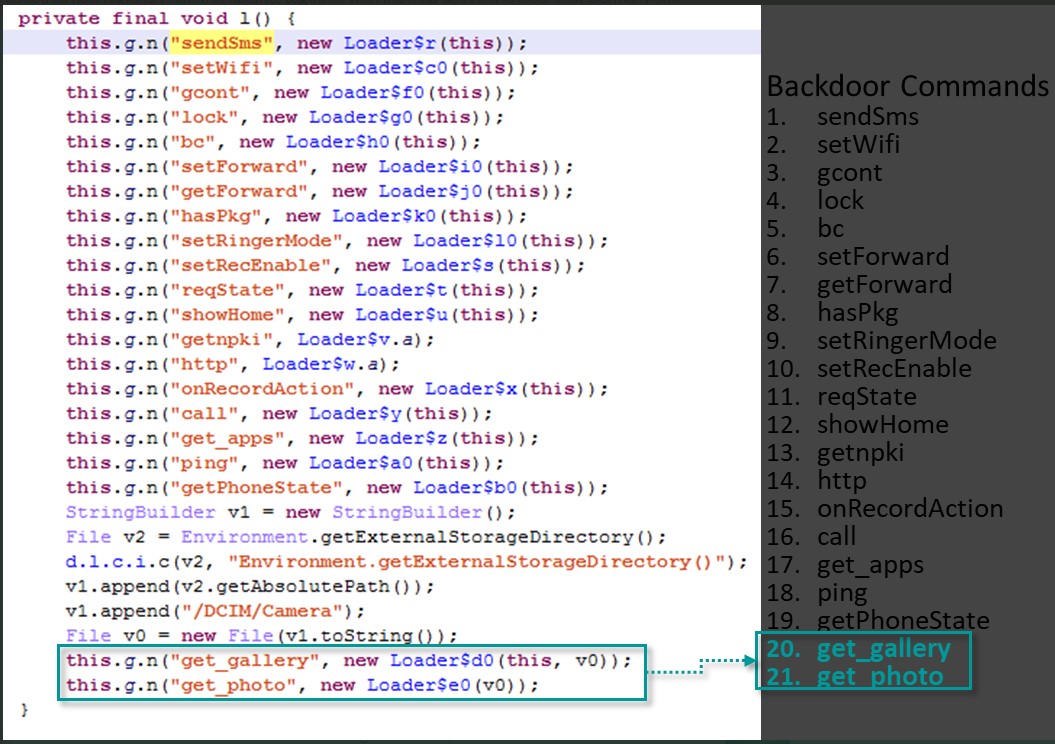
Source: Kaspersky
Kaspersky explains that threat actors may use the addition of these two new commands for financial fraud, identity theft, blackmail, and extortion if sensitive media is stolen.
“One possible scenario is that the criminals steal details from such things as driver’s licenses, health insurance cards or bank cards, to sign up for contracts with QR code payment services or mobile payment services,” Kaspersky explains in their report.
“The criminals are also able to use stolen photos to get money in other ways, such as blackmail or sextortion.”
Don’t get bit by the Mantis
To prevent Roaming Mantis and other Android malware from infecting your device, you should always avoid downloading APKs from unusual sources and never allow the installation of packages from unknown sources.
Furthermore, SMS texts that contain URLs should always be treated with caution and suspicion, even if they come from someone you know.
Finally, an Android internet security tool from a trusty vendor could help flag these URLs upon visiting them, as analysts actively track these campaigns.
Source: https://www.bleepingcomputer.com/news/security/roaming-mantis-android-malware-campaign-sets-sights-on-europe/


















