
Phishing campaign targets CoinSpot cryptoexchange 2FA codes

A new phishing campaign that targets CoinSpot cryptocurrency exchange users employs a new theme revolving around withdrawal confirmations with the end goal of stealing two-factor authentication (2FA) codes.
More specifically, the threat actors send emails from a Yahoo address, replicating real emails from CoinSpot that ask the recipients to confirm or cancel a withdrawal transaction.
These phishing messages also include details such as the transaction amount and a Bitcoin wallet address to add legitimacy to the attack.
Clicking on either of the embedded buttons on the email takes the victim to a phishing landing page that clones the CoinSpot login page and uses a domain name sufficiently close to the spoofed one not to attract the target’s attention.
.png)
“The style appears authentic, and there is even a Bitcoin address included to add to legitimacy. The user is prompted to either confirm or cancel the withdrawal, but both links have the same SendGrid hyperlink,” explains the Cofense report.
To further increase the “authentic” look of the phishing page, the threat actors also use a digital certificate that adds a lock symbol to the URL address bar to trick the visitor into thinking they’ve reached CoinSpot’s legitimate and secure login form.
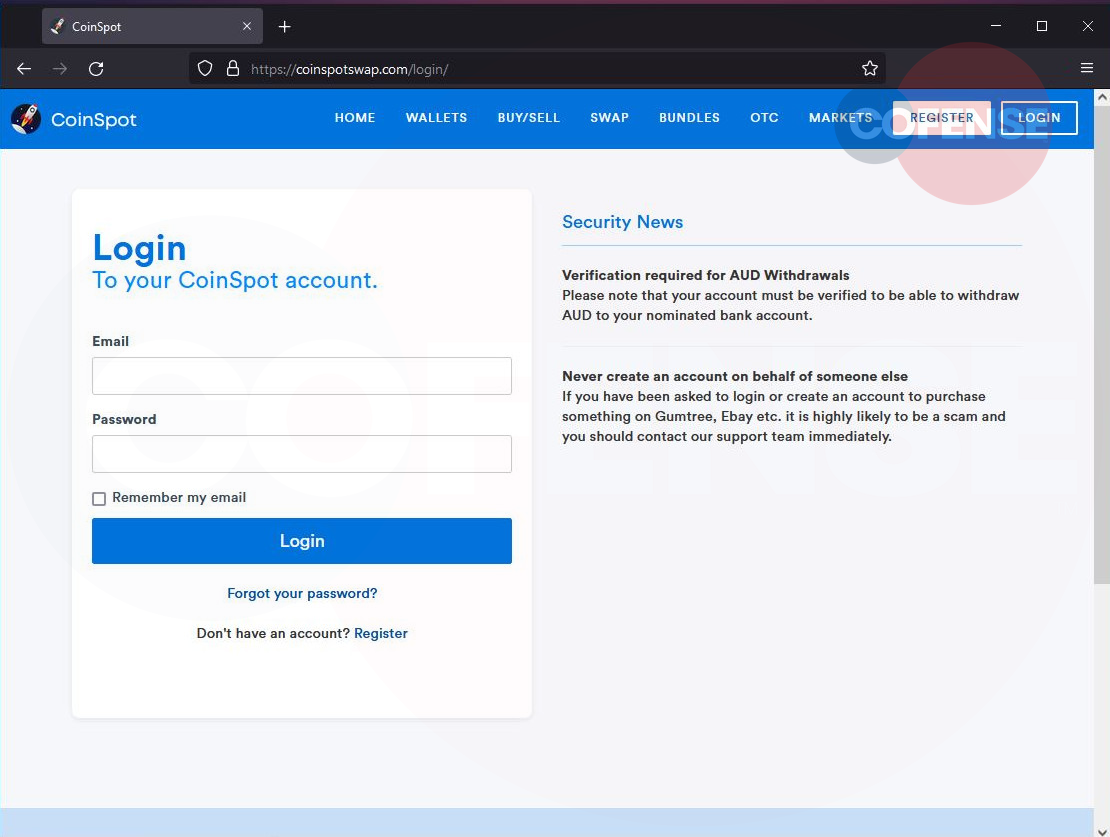
On the landing page, the victims are prompted to enter their account credentials on the phishing site, allegedly to verify or reject the transaction.
If they do that, they are served with a two-factor authentication page, which is the last protection measure against account takeover attempts.
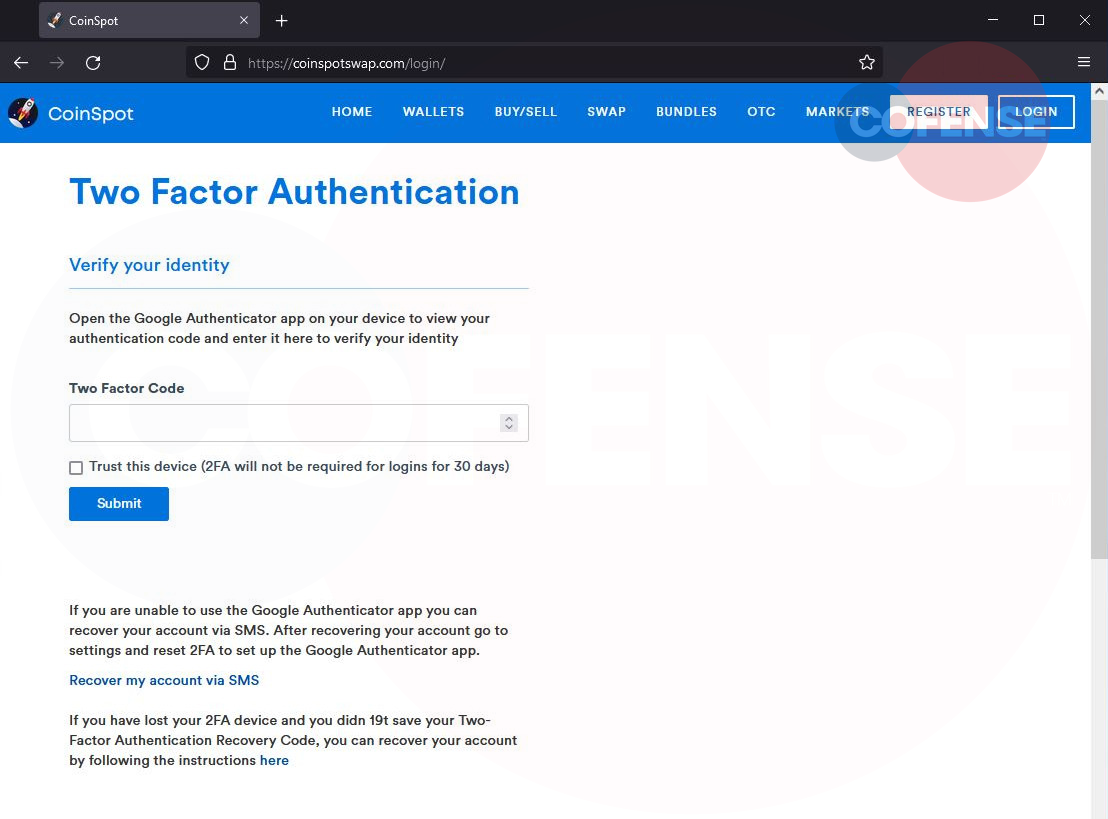
Source: Cofense
After entering their 2FA code, the victims are redirected to the official CoinSpot website in a final attempt to reduce the chances of raising suspicion.
The attackers can then use the account credentials and the stolen 2FA codes to take over the victim’s account. This is a time-sensitive act, indicating the scammers’ active involvement throughout the process.
Keep your crypto-investments secure
The hype around cryptocurrency investing creates a constant influx of inexperienced and potentially gullible users, which compels an ever-increasing number of threat actors to target the particular field.
This year, we have seen many different methods and tricks employed by phishing actors and scammers, from smishing and support scams to fake giveaways and malicious Google Ads.
In this case, even though the phishing email appears legitimate, the fact that it comes from a Yahoo email address is a clear sign of fraud.
Whenever you receive emails that ask you to take action, review basic elements such as the sender’s address calmly, and look for anything out of place.
Even if everything looks authentic, do not click on embedded email buttons. Instead, open a new tab on your browser, visit the official website manually, log in to your account, and check for any alerts or messages that require your attention.
For a complete list of security recommendations from CoinSpot on how to secure your devices and protect yourself from scammers, check out this support page.
Source: https://www.bleepingcomputer.com/news/security/phishing-campaign-targets-coinspot-cryptoexchange-2fa-codes/















