
Large-scale phishing study shows who bites the bait more often


A large-scale phishing study involving 14,733 participants over a 15-month experiment has produced some surprising findings that contradict previous research results that formed the basis for popular industry practices.
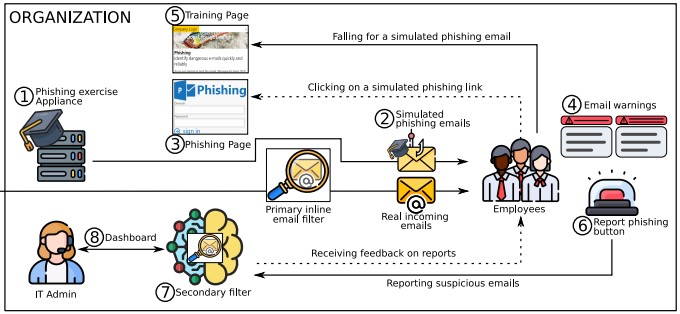
The study was conducted by researchers at ETH Zurich in collaboration with an unnamed company that did not inform the participants about the simulated phishing program.
To conduct the test, the researchers sent fake phishing emails to participants’ regular work email and deployed an email client button that allowed them to report suspicious emails easily.
Source: Arxiv.org
The four goals of the study were to determine:
- Which employees fall for phishing
- How vulnerability evolves over time
- How effective embedded training and warnings are
- Whether employees can do anything to help in phishing detection.
Gender is irrelevant
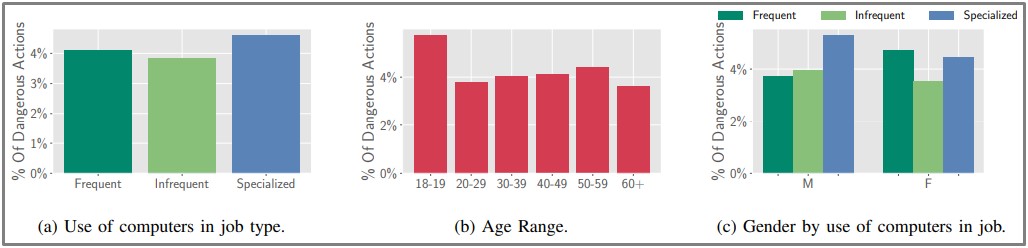
The demographics were diverse and allowed the researchers to look into an element presented as a crucial susceptibility determining factor.
One finding that contradicts existing studies is that gender does not correlate with phishing susceptibility.
Instead, the study found that younger and older people are more prone to clicking on phishing links, so age is a key factor.
Moreover, those who use specialized software for repetitive tasks are more likely to fall for phishing traps compared to those who do not need computers for their day-to-day jobs.
Source: Arxiv.org
Repeated clickers
The so-called “repeated clickers” highlighted in previous research also appear here with 30.62% of those who opened a simulated phishing email, clicked on additional emails. Furthermore, 23.91% of those performing a dangerous action (enabling macros, submitting credentials), did it more than once.
An interesting finding in the ETH study is that employees who are continuously exposed to phishing eventually fall for it, as 32.1% of the study participants clicked on at least one dangerous link or attachment.
This finding underlines the importance of having effective email security and anti-phishing filters in place, as constant exposure leads to numbness and risky actions even by resilient employees.
Training is overrated
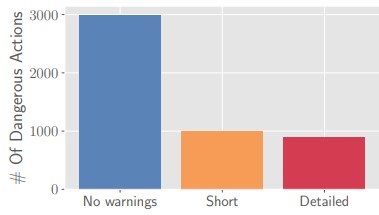
Warnings on suspicious emails were found to be effective, but this effectiveness didn’t grow as the warning messages got more detailed, which is a new finding.
Source: Arxiv.org
One finding that goes against commonly used security practices is that the researchers found that voluntary embedded training in simulated phishing exercises is ineffective.
“Interestingly, contradicting prior research results and a common industry practice, we found that the combination of simulated phishing exercises and voluntary embedded training (i.e., employees were not required to complete the training) not only failed to improve employee’s phishing resilience, but it actually even the made employees more susceptible to phishing” explains the research paper.
Crowd-sourcing is feasible
Employees in the tested company were given a ‘Report Phishing’ button on their email client to report suspicious messages.
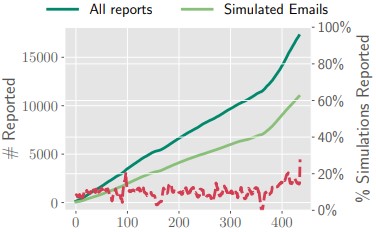
The study found that 90% of the employees reported six or fewer suspicious emails, but some remained very active throughout the experiment.
As such, the researchers conclude that there is no “reporting fatigue,” suggesting that crowd-sourcing anti-phishing data is feasible.
Source: Arxiv.org
In terms of the effectiveness of such as system, the analysts looked into reaction time and flagging accuracy.
The user reports were accurate in 68% for phishing and 79% if spam is accounted for as well, while the most prolific reporters reached an accuracy of over 80%.
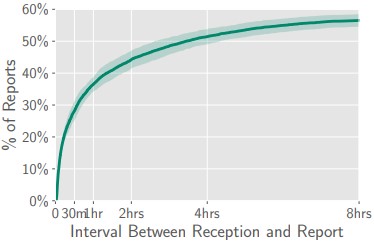
The time for these reports to be submitted after reception is 5 minutes for 10% of the total volume and half an hour for 35% of the total number of reports.
Source: Arxiv.org
“To apply these numbers to a hypothetical company of 1,000 employees where 100 of them are targeted by a phishing campaign, we would have between 8 and 25 reports of the email by employees—of which one within 5 minutes with high probability, and a larger number within 30 minutes,” details the paper.
These findings show that utilizing a corporate-wide crowd-sourced phishing detection service could significantly reduce the threat of phishing attacks.
It is also important to note that such a system wouldn’t produce a sizable operational workload as a result, so a corporation implementing crowd sourced phishing protection wouldn’t incur much additional burden.
Of course, phishing is a complicated topic involving many crucial factors beyond the scope of studies like this one, so these findings cannot be considered concrete evidence of good or bad practices or universally applicable rules.
However, considering the central role that phishing continues to play in the entire spectrum of modern cyber-attacks, one owes to build upon these findings by experimenting further to develop more effective anti-phishing measures.
Source: https://www.bleepingcomputer.com/news/security/large-scale-phishing-study-shows-who-bites-the-bait-more-often/


















