Windows 365 exposes Microsoft Azure credentials in plaintext

.jpg)
A security researcher has figured out a way to dump a user’s unencrypted plaintext Microsoft Azure credentials from Microsoft’s new Windows 365 Cloud PC service using Mimikatz.
Mimikatz is an open-source cybersecurity project created by Benjamin Delpy that allows researchers to test various credential stealing and impersonation vulnerabilities.
“It’s well known to extract plaintexts passwords, hash, PIN code and kerberos tickets from memory. mimikatz can also perform pass-the-hash, pass-the-ticket, build Golden tickets, play with certificates or private keys, vault, … maybe make coffee?,” explains the project’s GitHub page.
While created for researchers, due to the power of its various modules, it is commonly used by threat actors to dump plaintext passwords from the memory of the LSASS process or perform pass-the-hash attacks using NTLM hashes.
Using this tool, threat actors can spread laterally throughout a network until they control a Windows domain controller, allowing them to take over the Windows domain.
Windows 365 credentials can be dumped in plaintext
On August 2nd, Microsoft launched their Windows 365 cloud-based desktop service, allowing users to rent Cloud PCs and access them via remote desktop clients or a browser.
Microsoft offered free trials of virtual PCs that quickly ran out as people rushed to get their free Cloud PC for two months.
Delpy told BleepingComputer that he was one of the lucky few who could get a free trial and began testing the new service’s security.
He found that the brand new service allows a malicious program to dump the Microsoft Azure plaintext email address and passwords for logged-in users.
— Benjamin Delpy (@gentilkiwi) August 7, 2021
The credential dumps are being done through a vulnerability he discovered in May 2021 that allows him to dump the plaintext credentials for users logged into a Terminal Server.
While a user’s Terminal Server credentials are encrypted when stored in memory, Delpy says he could trick the Terminal Service process into decrypting them for him.
“Even better, I asked the terminal server process to decrypt them for me (and technically, terminal server process ask the kernel to decrypt it for itself),” Delpy told BleepingComputer in a conversation about his findings.
“Because only the Terminal Server can ask for this kind of own decryption, I had to trick it to decrypt the credentials for me :),”
BleepingComputer used a free Cloud PC trial on Windows 365 to test this technique. After connecting through the web browser and launching mimikatz with Administrative privileges, we entered the “ts::logonpasswords” command and mimikatz quickly dumped our login credentials in plaintext, as shown below.
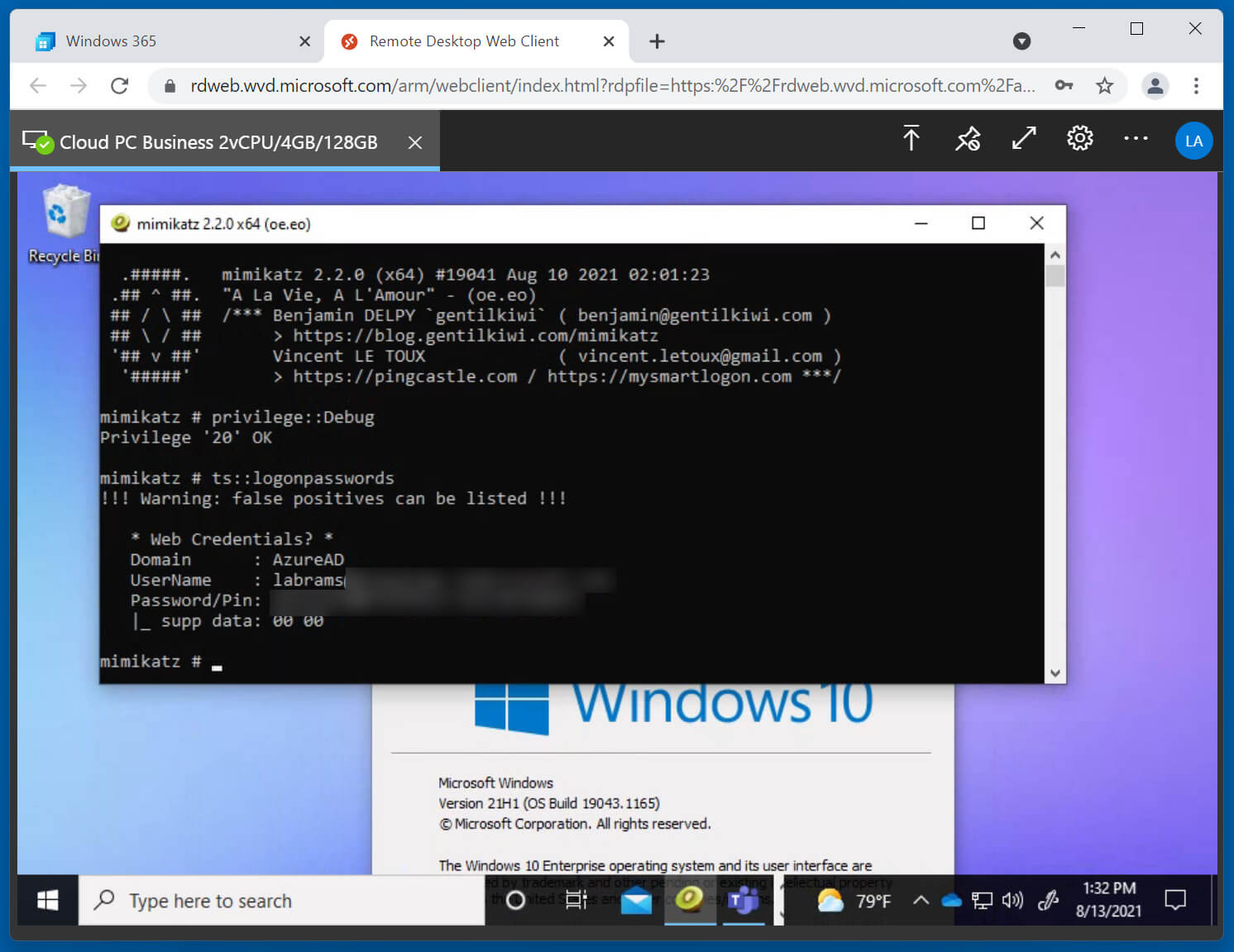
This works over the web browser as it’s still using the Remote Desktop Protocol.
So, what’s the big deal?
You may be wondering what the big deal is if you need to be an Administrator to run mimikatz and you already know your Azure account credentials.
In the above scenario, you are right, and it is not a big deal.
However, what happens if a threat actor gains access to your Windows PC device to run commands?
For example, let’s say that you open a phishing email with a malicious attachment on your Windows 365 Cloud PC that sneaks through Microsoft Defender.
Once you enable the malicious macros in the document, it can install a remote access program so that a threat actor can access the Cloud PC.
From there, it is trivial to gain administrative privileges using a vulnerability like PrintNightmare and then dump your clear-text credentials with mimikatz.
Using these credentials, the threat actor can spread laterally through other Microsoft services and potentially a company’s internal network.
“It’s exactly like dumping passwords from a normal session. If I can dump your password in TS sessions I can use it on other systems where you can have more privilege, data, etc,” explained Delpy.
“It’s common for lateral movements and gaining access to more privileged data on others systems. Particularly useful on VDI systems where others users are also logged in.”
Delpy says he would typically recommend 2FA, smart cards, Windows Hello, and Windows Defender Remote Credential Guard to protect against this method. However, these security features are not currently available in Windows 365.
As Windows 365 is geared towards the enterprise, Microsoft will likely add these security features in the future, but for now, it is important to be aware of this technique.
Source: https://www.bleepingcomputer.com/news/microsoft/windows-365-exposes-microsoft-azure-credentials-in-plaintext/