Microsoft adds Fusion ransomware attack detection to Azure Sentinel


Microsoft says that the Azure Sentinel cloud-native SIEM (Security Information and Event Management) platform is now able to detect potential ransomware activity using the Fusion machine learning model.
Azure Sentinel uses built-in artificial intelligence (AI) technology to quickly analyze vast volumes of data across enterprise environments, hunting for potential threat actor activity.
It also employs machine learning tech known as Fusion to detect and trigger multi-stage attack alerts by identifying sets of suspicious activities and abnormal behavior spotted at various attack stages.
Azure Sentinel couples several of these alerts to generate incidents even when there’s limited or missing information, making them highly difficult to catch otherwise.
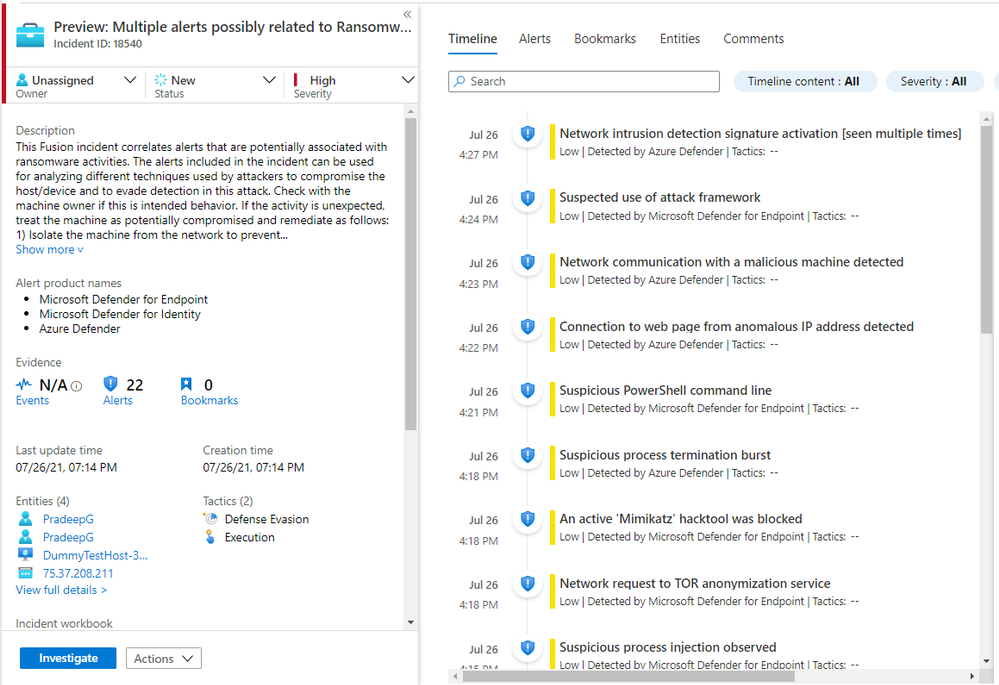
Microsoft announced today that its cloud-based SIEM now supports Fusion detections for possible ransomware attacks and triggers high severity Multiple alerts possibly related to Ransomware activity detected incidents.
For instance, Azure Sentinel will generate ransomware attack incidents after detecting the following alerts within a specific timeframe on the same host:
- Azure Sentinel scheduled alerts (informational): Windows Error and Warning Events
- Azure Defender (medium): ‘GandCrab’ ransomware was prevented
- Microsoft Defender for Endpoint (informational): ‘Emotet’ malware was detected
- Azure Defender (low): ‘Tofsee’ backdoor was detected
- Microsoft Defender for Endpoint (informational): ‘Parite’ malware was detected
To detect potential ongoing ransomware attacks, Azure Sentinel can use the following data connectors to collect data from the following sources: Azure Defender (Azure Security Center), Microsoft Defender for Endpoint, Microsoft Defender for Identity, Microsoft Cloud App Security, and Azure Sentinel scheduled analytics rules.
Admins advised to consider systems as ‘potentially compromised’
“Incidents are generated for alerts that are possibly associated with Ransomware activities, when they occur during a specific time-frame, and are associated with the Execution and Defense Evasion stages of an attack,” Microsoft explains.
“You can use the alerts listed in the incident to analyze the techniques possibly used by attackers to compromise a host/device and to evade detection.”
Following a ransomware attack scenario detected by Fusion in Azure Sentinel, admins are advised to consider the systems as “potentially compromised” and take immediate actions.
Microsoft provides the following recommended steps for analyzing the techniques used by attackers during the potential attack:
- Isolate the machine from the network to prevent potential lateral movement.
- Run a full antimalware scan on the machine, following any resulting remediation advice.
- Review installed/running software on the machine, removing any unknown or unwanted packages.
- Revert the machine to a known good state, reinstalling the operating system only if required and restoring software from a verified malware-free source.
- Resolve recommendations from alert providers (e.g., Azure Security Center and Microsoft Defender) to prevent future breaches.
- Investigate the entire network to understand the intrusion and identify other machines that might be impacted by this attack.
Source: https://www.bleepingcomputer.com/news/microsoft/microsoft-adds-fusion-ransomware-attack-detection-to-azure-sentinel/