
Prometheus: The $250 service behind recent malware attacks


Security researchers investigating multiple malware distribution campaigns found that an underground traffic distribution service called Prometheus is responsible for delivering threats that often lead to ransomware attacks.
Among the malware families that Prometheus TDS has dished out so far are BazarLoader, IcedID, QBot, SocGholish, Hancitor, and Buer Loader, all of them commonly used in intermediary attack stages to download more damaging payloads.
Trojan delivery service
A traffic direction system (TDS) allows redirecting users to content based on specific characteristics (e.g. location, language, device type) that determine further action.
Threat actors have been using such tools for more than a decade. A 2011 report from Trend Micro details an upgrade of the Koobface botnet with a TDS component that increased profits by driving traffic to affiliate advertising websites.
Researchers at cybersecurity company Group-IB found that the Prometheus TDS malware-as-a-service (MaaS) operation is being advertised on underground forums since at least August 2020 for $250 per month.
A user called Main is promoting it as a “professional redirect system” with anti-bot protection that is suitable for email marketing, generating traffic, and social engineering.
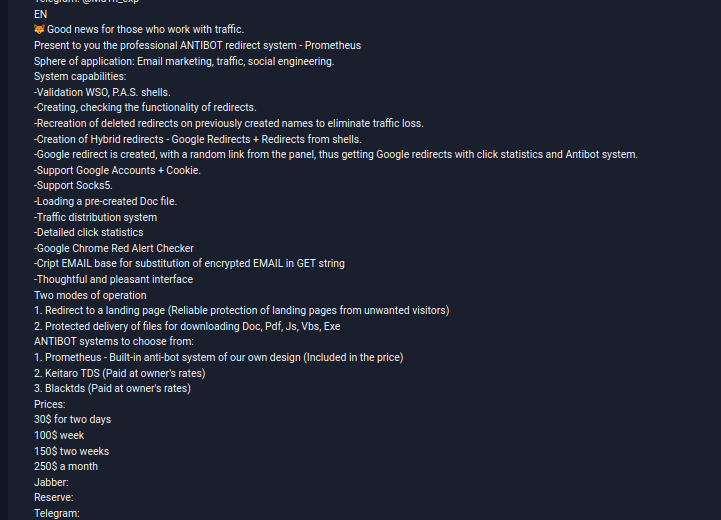
Prometheus uses a network of websites infected with a backdoor accessible from the service’s administration panel, where customers can create a profile for their targets.
The researchers say that users can be redirected to a website infected with Prometheus.Backdoor through an email campaign delivering an HTML file with a redirect, or a link to a web shell leading to a compromised site, or a Google document pointing to the malicious URL.
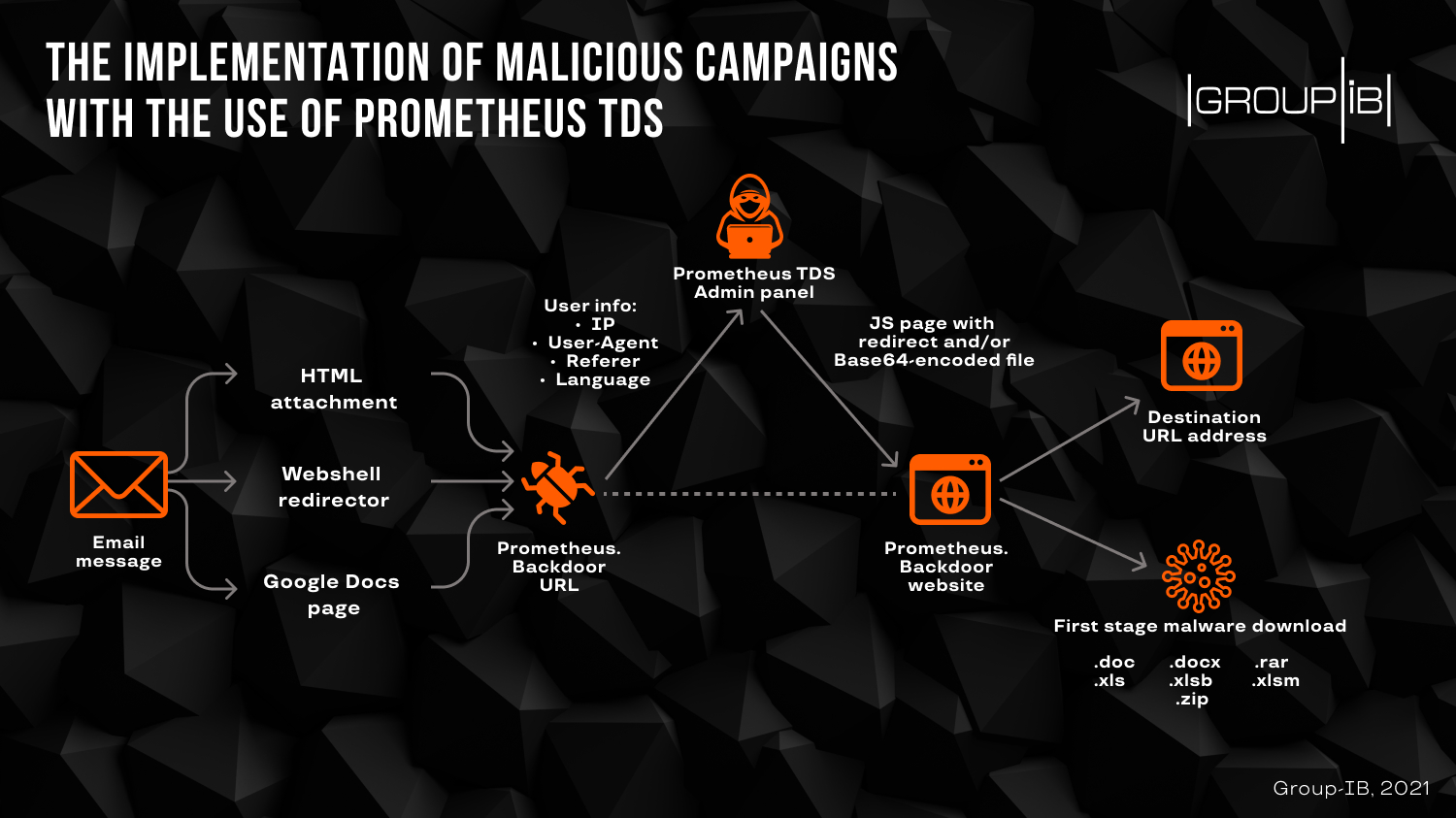
When users land on the hacked website, the PHP-based Prometheus.Backdoor collects the connection details (IP address, user agent, referrer header, time zone, language) and forwards them to the admin panel.
“If the user is not recognized as a bot, then, depending on the configuration, the administrative panel can send a command to redirect the user to the specified URL, or to send a malicious file. The payload file is sent using a special JavaScript code“ – Group-IB
The malicious code is often hidden in malicious Microsoft Word or Excel documents, although ZIP and RAR archives have also been used.
During their investigation, the Group-IB Threat Intelligence team found more than 3,000 target email addresses in campaigns that used Prometheus TDS.
Some of the targeted inboxes belonged to U.S. government agencies, companies, and corporations in the banking and finance, retail, energy and mining, cybersecurity, healthcare, IT, and insurance sectors.
When investigating the Prometheus TDS malware distribution campaigns, the researchers found dozens of malicious Office documents that delivered Campo Loader (a.k.a. BazarLoader), Hancitor, QBot, IcedID, Buer Loader, and SocGholish.
All of the above trojans are malware downloaders involved over the past year in earlier stages of a ransomware attack (WastedLocker, Ryuk, Egregor, RansomExx, REvil, Cuba, Conti).
However, the Group-IB Threat Intelligence team told BleepingComputer that they could not link the Prometheus TDS to ransomware attacks because they examined the malicious files in a virtual environment.
“Group-IB researchers examined the extracted malicious files in the virtual environment, while ransomware operators now tend to be selective, which means that after the network compromise they proceed with the lateral movement to find out more about the compromised company and decide whether it’s worth to encrypt its network. So possibly the virtual machines didn’t seem attractive enough to the cybercriminals” – Group-IB
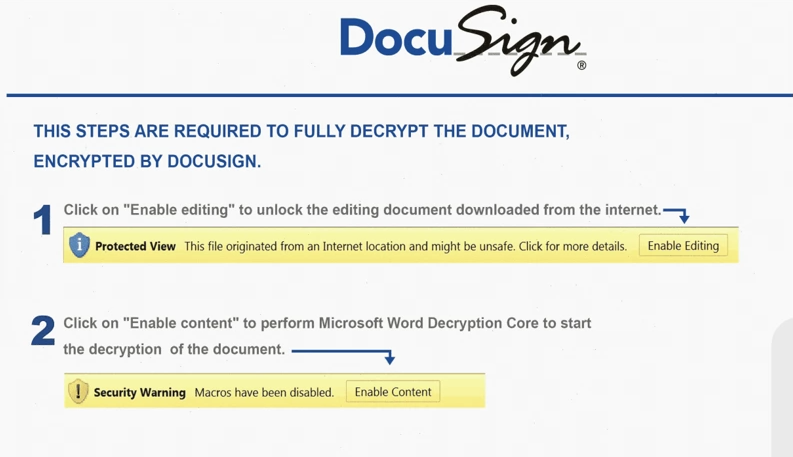
After downloading the malware, some of the malicious documents redirected users to legitimate websites (DocuSign, USPS), to mask the malware infection.
Fake VPN, spam, and password brute-forcing
Apart from malware, Prometheus TDS has also been used to redirect users to sites offering fake VPN solutions, selling pharmaceutical products (Viagra spam), or phishing pages for banking information.
Whoever is behind Prometheus is also running another service called BRChecker – a password brute-force tool, which shared the infrastructure used by the TDS service.
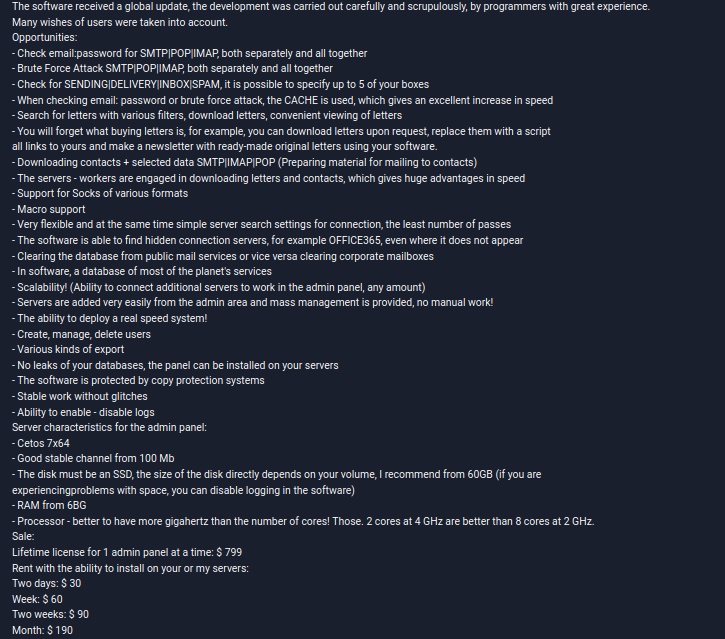
Group-IB found advertisements for BRChecker as old as mid-June 2018 from a user called Mainin, a handle very similar to the one promoting Prometheus.
The researchers told BleepingComputer that the overlaps in functionality and infrastructure indicate that both services have the same developer.
The two systems are active, as the researchers see new websites infected with Prometheus.Backdoor every day. Furthermore, admin panels appear regularly, a clear sign of new customers.
Source: https://www.bleepingcomputer.com/news/security/prometheus-the-250-service-behind-recent-malware-attacks/


















