
DarkSide ransomware gang returns as new BlackMatter operation


Encryption algorithms found in a decryptor show that the notorious DarkSide ransomware gang has rebranded as a new BlackMatter ransomware operation and is actively performing attacks on corporate entities.
After conducting an attack on Colonial Pipeline, the US’s largest fuel pipeline, and causing fuel shortages in the southeast of the USA, the DarkSide ransomware group faced increased scrutiny by international law enforcement and the US government.
In May, the DarkSide ransomware operation suddenly shut down after losing access to their servers and cryptocurrency was seized by an unknown third-party.
It was later learned that the FBI recovered 63.7 Bitcoins of the approximately 75 Bitcoin ($4 million) ransom payment made by Colonial Pipeline.
This week, a new ransomware operation known as BlackMatter emerged that is actively attacking victims and purchasing network access from other threat actors to launch new attacks.
BleepingComputer is aware of one victim who paid BlackMatter $4 million does this week to delete any stolen data and provide both Windows and Linux ESXi decryptors.
While researching the new ransomware group, BleepingComputer found a decryptor from a BlackMatter victim and shared it with Emisosft CTO and ransomware expert Fabian Wosar.
After analyzing the decryptor, Wosar confirmed that the new BlackMatter group is using the same unique encryption methods that DarkSide had used in their attacks.
After looking into a leaked BlackMatter decryptor binary I am convinced that we are dealing with a Darkside rebrand here. Crypto routines are an exact copy pretty much for both their RSA and Salsa20 implementation including their usage of a custom matrix.
— Fabian Wosar (@fwosar) July 31, 2021
Wosar told BleepingComputer that the encryption routines used by BlackMatter are pretty much the same, including a custom Salsa20 matrix unique to DarkSide.
When encrypting data using the Salsa20 encryption algorithm, a developer provides an initial matrix consisting of sixteen 32-bit words.
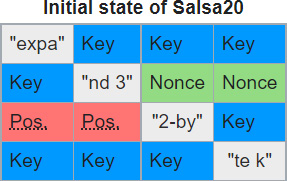
Source: Wikipedia
When encrypting files, Fabian told BleepingComputer that instead of using constant strings, a position, nonce, and key, for each encrypted file, DarkSide fills the words with random data.
This matrix is then encrypted with a public RSA key and stored in the footer of the encrypted file.
Fabian says this Salsa20 implementation was previously only used by DarkSide, and now BlackMatter.
BleepingComputer was also told that DarkSide used an RSA-1024 implementation unique to their encryptor, which BlackMatter also uses.
While there is not 100% proof that BlackMatter is a rebrand of the DarkSide operation, many similar characteristics make it hard to believe this is not the case.
When we take the same encryption algorithms, the similar language used on the BlackMatter sites, similar craving of media attention, and similar color themes for their TOR sites, it is highly like that BlackMatter is the new DarkSide.
A rebrand from DarkSide also explains the reason the new BlackMatter group won’t target the “Oil and Gas industry (pipelines, oil refineries),” which led to their previous downfall.
Unfortunately, this is a highly skilled group that targets multiple device architectures, including Windows, Linux, and ESXi servers.
Due to this, we will need to keep an eye on this new group as they will surely perform attacks on well-known targets in the future.
Source: https://www.bleepingcomputer.com/news/security/darkside-ransomware-gang-returns-as-new-blackmatter-operation/


















