How to mitigate Print Spooler vulnerability on Windows 10

Yesterday, Microsoft released multiple Windows updates to fix the widely reported “PrintNightmare” vulnerability in the Windows Print Spooler service.
According to Microsoft, this vulnerability is impacting all Windows 10 versions, including the most recent May 2021 Update (version 21H1) and version 20H2 (October 2020 Update).
To deploy Microsoft’s patch, you need to check for updates under Updates & Security > Windows Update and apply the latest July update, and reboot the system when prompted.
Alternatively, you can install the emergency update manually from the Microsoft Update catalog if you are unable to do so via the normal Windows Update procedure.
However, researchers have revealed that Microsoft’s patch is incomplete and attackers can still abuse the vulnerability to gain access to the system. Thankfully, you can temporarily disable the Windows Print Spooler service to mitigate the vulnerability until a proper fix is released.
In this guide, we will highlight the steps to disable the Windows Print Spooler service and mitigate the PrintNightmare CVE-2021-34527 vulnerability.
Disable Print Spooler service on Windows 10 using PowerShell
To mitigate the PrintNightmare vulnerability using PowerShell, follow these steps:
- Right-click on the Start Menu or press Windows+X.
- Click “Windows PowerShell (Admin).”
.jpg)
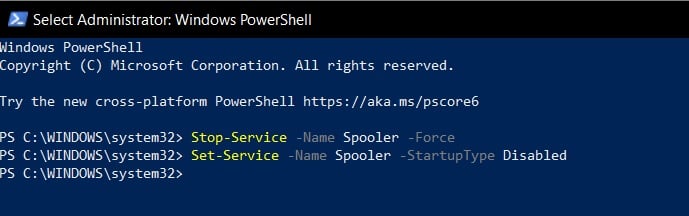
Open PowerShell - Enter the following command to stop the Spooler service:
Stop-Service -Name Spooler -Force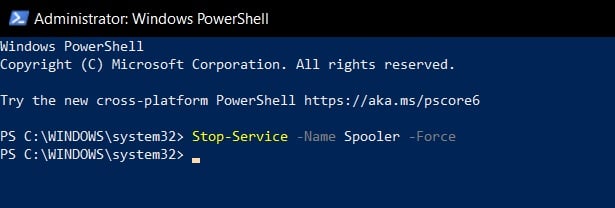
Disable Print Spooler - Enter the following command to block Print service from starting again in future.
Set-Service -Name Spooler -StartupType Disabled
Block Print Spooler service - Close PowerShell window.
If you want to re-enable the Print Spooler service, follow these steps
- Right-click on the Start Menu or press Windows+X.

Open PowerShell - Click “Windows PowerShell (Admin).”
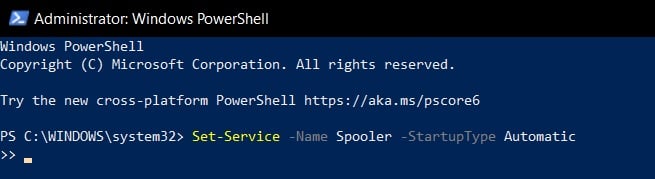
- Enter the following command to enable the Spooler service:
Set-Service -Name Spooler -StartupType Automatic
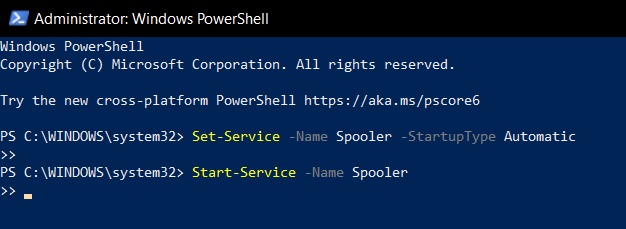
Enable Print Spooler - Enter the following command to restart Print service:
Start-Service -Name Spooler
Start Print Spooler - Close PowerShell window.
Disable Print Spooler service on Windows 10 using Group Policy editor
To mitigate the PrintNightmare vulnerability using Group Policy editor on Windows 10 Pro and Enterprise, follow these steps:
- Open Start Menu or Windows Search and enter gpedit.msc to open the Local Group Policy Editor.
- In Group Policy editor, navigate to the following path: Computer Configuration > Administrative Templates > Printers
- Double-tap the Allow Print Spooler to accept client connections policy.
- Select the Disabled option.
- Tap on the Apply button and select OK.
When the policy is disabled, Microsoft says the spooler will automatically reject the client connections and prevent users from sharing printers. However, all printers currently shared will continue to be shared.
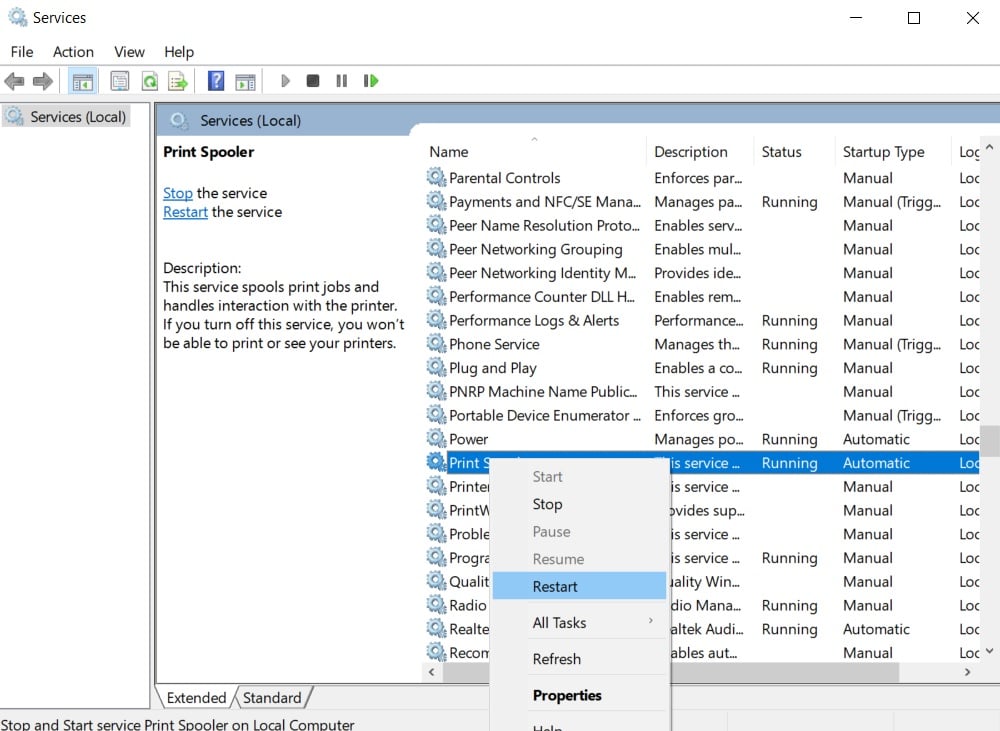
The spooler must be restarted for changes to this policy to take effect. To restart the spooler service, follow these steps:
- Open Start menu.
- Type “Services”
- Double-click “Printer Spooler” in the Services list.

Restart Print Spooler service - Click Restart.
- Click OK.
If you want to re-enable Print Spooler using Group Policy editor, follow these steps:
- Open Start Menu and enter gpedit.msc to open the Local Group Policy Editor.
- In Group Policy editor, navigate to the following path: Computer Configuration > Administrative Templates > Printers
- Double-tap the Allow Print Spooler to accept client connections policy.
- Select the Not configured or Enabled option.
- Tap on the Apply button and select OK.
Source: https://www.bleepingcomputer.com/news/microsoft/how-to-mitigate-print-spooler-vulnerability-on-windows-10/