
Report highlights top 10 threat detections seen across Microsoft Azure AD and Office 365
A new report from cybersecurity company Vectra has highlighted the top ten threats their customers face when using Microsoft Azure AD and Office 365.
The list in the “2021 Q2 Spotlight Report: Top 10 Threat Detections for Microsoft Azure AD and Office 365” is topped by O365 risky exchange operations, Azure AD suspicious operations and O365 suspicious download activity.
Between January and March, Vectra saw a startling increase in detections centered on attackers trying to manipulate Exchange in order to gain access to specific data or further attack progression. More than 70% of Vectra’s customers triggered that detection per week, according to their data.
More than 60% of Vectra customers also triggered weekly detections of abnormal Azure AD operations, meaning cyberattackers may be escalating privileges and performing admin-level operations after regular account takeover. O365 accounts downloading unusual numbers of objects was also high on the list of detections caught weekly, followed by other issues with O365 related to suspicious sharing activity and external team access.
Other commonly seen detections by Vectra include administrative privileges being assigned to redundant accounts or suspicious mail forwarding.
The study notes that many of the functions being targeted are used to share files and access with other users within a company, making it difficult to defend as more people work from home and have no choice but to share files digitally.
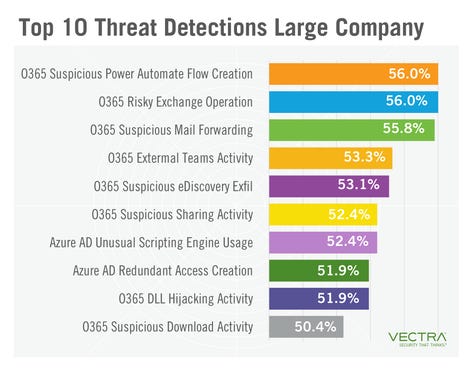
There were some differences with the kind of detection trends noticed at small, medium and large companies. While smaller organizations dealt with more O365 risky exchange operations, Azure AD suspicious operations and O365 suspicious download activity, larger entities had to face more O365 suspicious power automate flow creation detections as well as more suspicious mail forwarding and external team activity in O365.
Vectra
Overall, larger companies generally triggered less detections, and researchers with Vectra surmised that users and administrators from larger companies may “perform Office 365 and Azure AD activity more consistently compared to smaller organizations.”
But larger companies also had to face more Office 365 DLL hijacking, Office 365 unusual scripting engine attacks and Office 365 suspicious eDiscovery exfils, the report noted.
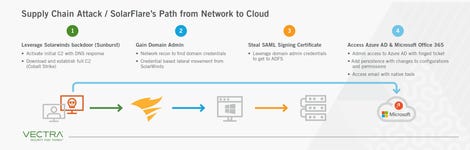
The study also includes a detailed breakdown of how the Solarwinds backdoor was being leveraged by attackers.
Vectra
Cybersecurity experts attributed much of the report’s findings to the massive shift to remote work that took place in 2020 due to the pandemic. There are over 250 million active Microsoft Office 365 users, and AppOmni CEO Brendan O’Connor, who said the pandemic exposed how seriously undermanned teams are when it comes to cybersecurity.
“When enterprises shifted to a virtual and remote workforce, organizations had to quickly shift business applications and data to the cloud. IT staff can no longer gain the little benefit they had from network segmentation afforded by traditional office networks,” he said.
“With traditional security measures completely removed from the equation, IT staff struggled to implement necessary measures to ensure the safety of data in the cloud. The rapid adoption of SaaS exposed not only the lack of general cybersecurity expertise but also the lack of expertise in SaaS to leverage the built-in security measures effectively.”















